Advanced security technologies make it possible to detect, analyze, and respond to incidents with impressive precision. Yet even the best tools can’t bridge the gaps created by disjointed responsibilities, siloed workflows, and competing priorities. This lack of cohesion weakens your security posture and increases exposure to sophisticated attacks that thrive on disorganization.
41% of organizations struggle to manage cybersecurity collaboratively. For organizations managing complex environments, from financial institutions to global e-commerce platforms, cyber fusion centers break down silos, establish clear responsibilities, and prioritize efforts—transforming disjointed defenses into a unified, proactive security posture.
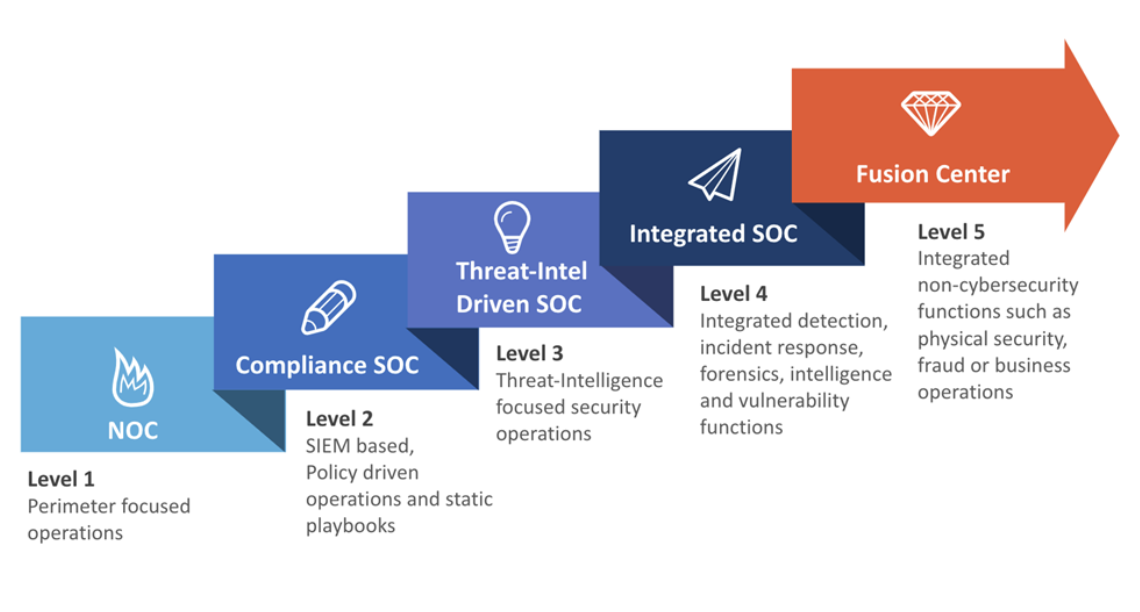
The Cyber Fusion Center as an Evolution of the SOC
A Cyber Fusion Center is a centralized hub designed to integrate cybersecurity efforts across teams, tools, and processes, enabling a proactive approach to threat management. While traditional Security Operations Centers (SOCs) focus primarily on monitoring and responding to security incidents, fusion centers expand this scope by unifying threat intelligence, risk assessment, vulnerability management, and strategic decision-making into a single operational framework. This holistic approach empowers businesses to detect, predict, and prevent threats with greater precision and agility.
What truly distinguishes cyber fusion centers is their emphasis on cross-team collaboration and intelligence-driven operations. By fostering shared workflows and real-time communication, they ensure faster, more coordinated responses to sophisticated threats. This integration not only enhances efficiency but also allows organizations to stay ahead of emerging risks with a more strategic and unified defense strategy.
Key Components of a Cyber Fusion Center
A cyber fusion center helps you deliver a cohesive, proactive cybersecurity approach that extends far beyond the capabilities of traditional SOCs.
1. Threat Intelligence Integration
At the heart of a cyber fusion center is its ability to integrate threat intelligence into daily operations. Unlike SOCs, which might rely on external or fragmented feeds, fusion centers consolidate intelligence from multiple sources into a unified data stream. This includes real-time feeds, open-source threat data, and internal telemetry, all processed and analyzed to provide a holistic view of the threat landscape.
2. Automation Frameworks
Fusion centers typically operate under various automation frameworks powered by security orchestration, automation, and response (SOAR) platforms. These frameworks automate repetitive tasks like alert triage, log correlation, and report generation. They rely on predefined playbooks to execute actions like quarantining endpoints, disabling user accounts, or generating escalation tickets without manual intervention.
3. Incident Response
A structured incident response capability is central to a cyber fusion center, ensuring rapid and coordinated actions during a security breach. By integrating predefined response playbooks and real-time collaboration tools, fusion centers streamline the containment and remediation of threats, minimizing potential damage and recovery time.
4. Governance and Compliance
Governance and compliance are essential components of a cyber fusion center, ensuring that all activities align with regulatory requirements and internal policies. Beyond meeting external compliance standards, effective governance also enforces internal policies and security best practices, maintaining accountability and consistency across operations.
Fusion centers include predefined modules for mapping security actions to regulatory requirements. These modules are configured with frameworks like ISO 27001, PCI DSS, and NIST 800-53, allowing for real-time tracking and auditing of compliance metrics. Role-based access control (RBAC) systems also ensure that only authorized personnel can access sensitive data or execute specific actions, reinforcing governance protocols.
5. Collaboration and Communication Tools
Collaboration and communication tools are the backbone of a fusion center’s ability to break down silos between teams. These tools provide a unified workspace for incident responders, analysts, and decision-makers, enabling seamless coordination and faster resolution of threats. The result is a more connected and efficient approach to cybersecurity management.
Think of these tools as the “property management service” of cybersecurity operations—ensuring that every asset, team member, and workflow is in the right place at the right time. By fostering a culture of collaboration, fusion centers eliminate inefficiencies caused by isolated workflows and limited visibility. Teams can align their efforts through shared dashboards, automated notifications, and real-time chat platforms. These features ensure that critical information flows smoothly across departments, allowing organizations to respond to threats with greater precision and speed.
6. Data Analytics
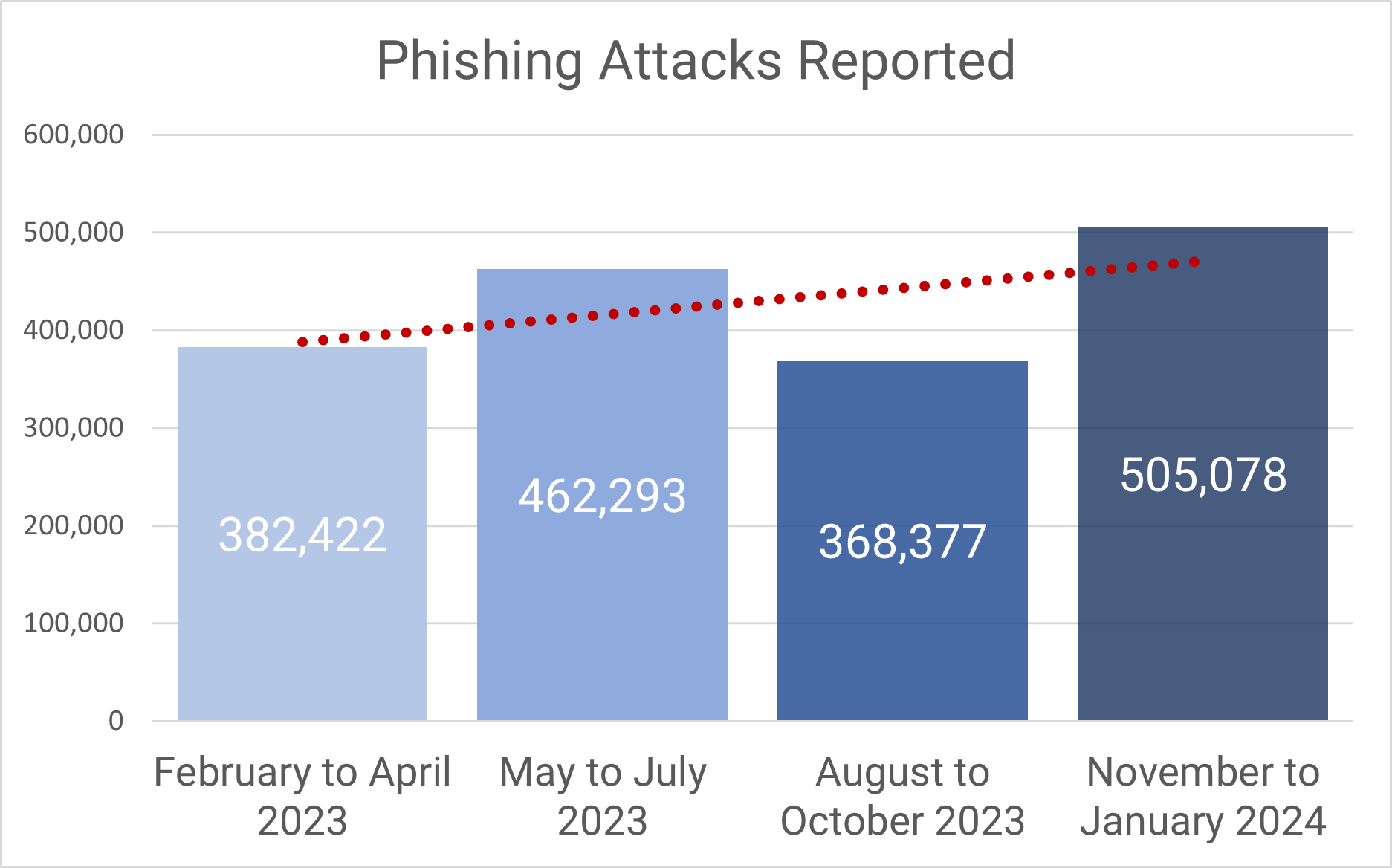
Traditional SOCs rely on basic rule-based systems to process the massive volume of logs from firewalls, endpoints, and cloud platforms. This leads to alert floods and wasted time on false positives. SOC teams spend 32% of their working day resolving false positive alerts.
Cyber fusion centers unify various datasets—from real-time threat feeds to logs and vulnerability scans—into a single, enriched source of truth. Using technologies like natural language processing (NLP), they integrate unstructured reports with structured data to provide analysts with deeper context.
7. Behavioral Analytics
Behavioral analytics plays a critical role in cyber fusion centers by identifying anomalies in user or attacker behavior. These insights enable early detection of sophisticated threats, such as insider attacks or evolving tactics, that traditional monitoring might miss. Behavioral analytics enhances the precision of detection and reduces false positives, improving overall efficiency.
Why Your Organization Needs a Cyber Fusion Center
While there are clear advantages to establishing a cyber fusion center, all traditional SOCs monitor, detect, and respond to threats. Shouldn’t that be enough? The reality is today’s threats are faster, smarter, and more coordinated; they exploit the silos and lack of cross-team coordination that SOCs can’t overcome. Here’s how a cyber fusion center can break down these barriers.
1. Protection in an Evolving Threat Landscape
Attackers constantly refine their tactics to exploit blind spots. Cyber fusion centers adapt to this evolving threat landscape by unifying threat intelligence with real-time analytics. When zero-day vulnerabilities emerge, or adversaries deploy sophisticated tactics like supply chain attacks, a fusion center detects patterns faster and coordinates a response across your teams. You gain the ability to spot attacks that combine multiple threat vectors, such as phishing or smishing communications linked to credential theft and lateral movement.
2. Proactive Risk Management
Cyber fusion centers offer proactive risk management by combining threat modeling, vulnerability assessments, and predictive analytics. Instead of waiting for attackers to exploit a vulnerability, the fusion center anticipates and mitigates internal and vendor risks in advance.
For example, if external threat intelligence indicates a spike in ransomware activity, the fusion center aligns your vulnerability patching efforts with known attack vectors or segments of the network to bolster critical systems before the threat reaches you. This proactive approach minimizes the likelihood of a successful attack and strengthens your overall security posture.
3. Scalability and Adaptability
Cyber fusion centers are designed to grow and evolve alongside your organization. As your business scales or faces new challenges, fusion centers can seamlessly integrate additional tools, processes, and workflows to meet expanding requirements. They are built to adapt to emerging threats and shifting regulatory landscapes, ensuring your organization remains resilient and secure in an ever-changing environment.
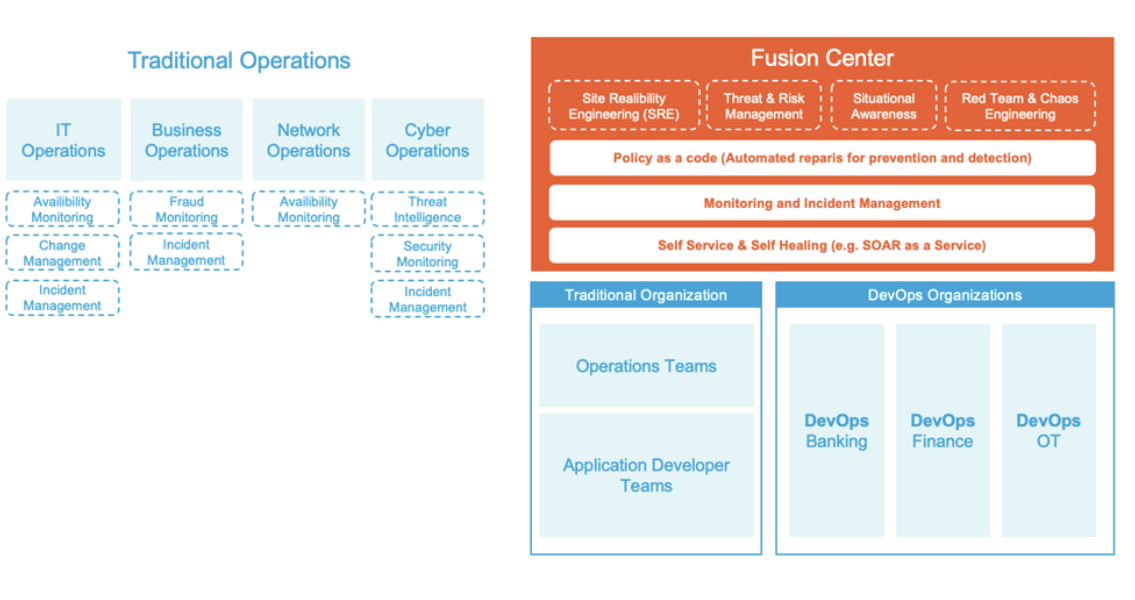
4. Enhanced Interdepartmental Collaboration
Silos don’t just slow down response times; they create gaps in your defenses. A cyber fusion center breaks down these silos by fostering collaboration between teams like IT, risk management, and compliance. Everyone shares the same intelligence, operates under unified priorities, and works toward the same goals.
When a potential breach occurs, the fusion center ensures that IT teams, security analysts, and compliance officers coordinate their actions seamlessly. Instead of separate teams addressing isolated pieces of an attack, all stakeholders contribute to a single, coordinated response.
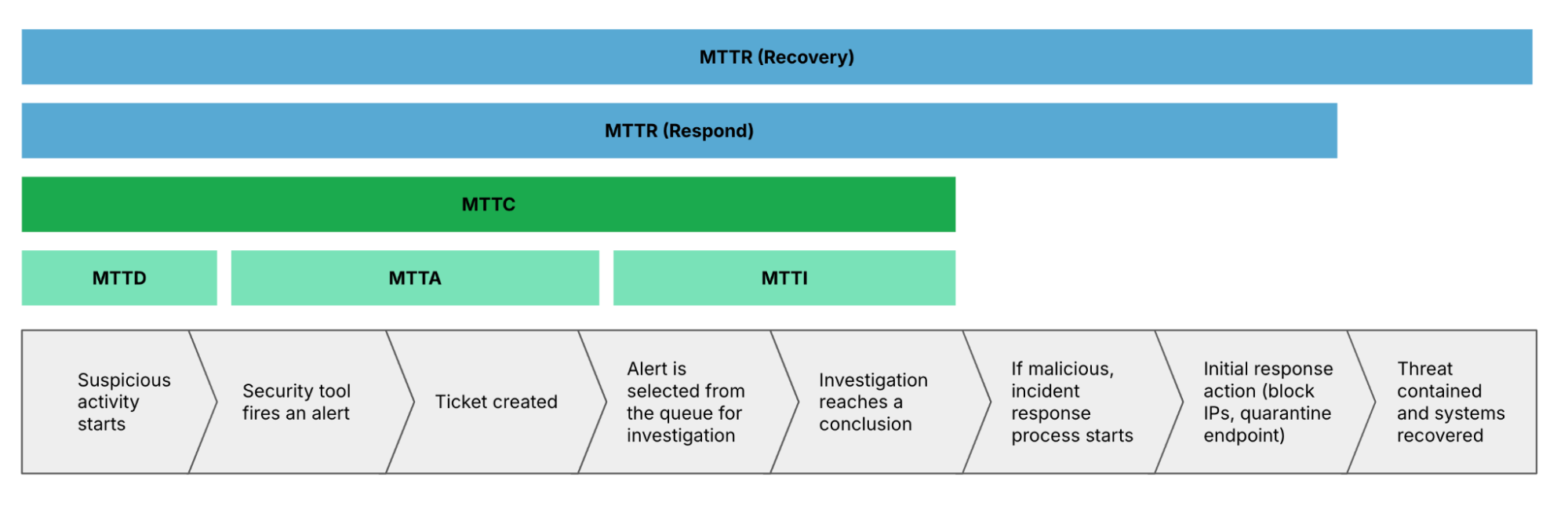
5. Reduced Mean Time to Detect (MTTD) and Respond (MTTR)
Cyber fusion centers excel at reducing MTTD and MTTR by integrating automated workflows, adaptive algorithms, and shared intelligence. For example, when a suspicious login attempt occurs, the fusion center doesn’t just flag it—it immediately correlates it with other events, such as unusual file access or anomalous user behavior.
Fusion centers eliminate delays caused by manual processes by automating low-level triage and escalating only relevant alerts. Your analysts receive enriched, actionable data instead of vague, disconnected alerts. This streamlined approach enables you to contain threats before they escalate, saving time, money, and reputational damage.
6. Continuous Improvement Through Threat Feedback Loops
In cyber fusion centers, the team uses what they have learned from each incident to refine processes and improve defenses. SOCs often lack the capacity for this continuous improvement because they are buried under false-positive alerts, disjointed data streams, and manual workflows. With your analysts spending most of their time reacting to low-priority alerts, there’s little bandwidth left for strategic refinement.
Fusion centers solve this by automating alert triage and consolidating intelligence so teams can focus on meaningful insights. For example, instead of treating a phishing attack as isolated, a fusion center correlates it with broader trends, like a rise in impersonation attempts targeting executives. This insight helps strengthen defenses, improving response strategies like blocking malicious domains, updating email filters, and conducting targeted security training for vulnerable teams.
Fraud Detection in the Era of Cyber Fusion Centers
Digital fraud often operates beyond the reach of traditional security tools, making its inclusion in your cyber fusion center essential. Attackers exploit tactics like website impersonation, fake domains, and phishing campaigns to deceive customers and employees, bypassing standard SOC monitoring. A real-time fraud detection capability integrated within your fusion center addresses these gaps, providing continuous monitoring and actionable intelligence to combat sophisticated attacks.
Memcyco is at the forefront of this evolution, offering solutions that deliver real-time protection, proactive fraud prevention, and detailed insights into attacks, attackers, and victims. For example, Memcyco’s tools can identify website cloning in real time, providing information on the attacker’s device, location, and potential victims. These capabilities empower organizations across industries—such as financial services, retail, and hospitality—to protect customers, secure revenue, and safeguard reputations.
A cyber fusion center’s unified structure amplifies the value of fraud detection by seamlessly integrating it with threat intelligence, incident response, and behavioral analytics. This interconnected approach ensures that fraud isn’t treated as an isolated issue but as a vital component of your overall security posture, enabling businesses to predict, prevent, and neutralize threats before they escalate.
To learn more about how Memcyco can enhance your organization’s fraud detection strategy, visit our website.