Reverse proxy phishing has quietly become one of the most effective –and hardest to detect– phishing tactics of the modern era. It’s fast, industrialized, and invisible to most security stacks. Instead of tricking users into handing over static credentials, these attacks use real-time relays to bypass MFA and hijack sessions as they happen.
EvilProxy, Frappo, Muraena – just three off-the-shelf phishkits bad actors use, not to merely capture static credentials, but to gain full access to live sessions. That means account takeover isn’t just possible, it’s immediate. If your current protections can’t detect live phishing proxies or the behavioral signals that often precede session hijack, you are already behind the curve.
What Is Reverse Proxy Phishing?
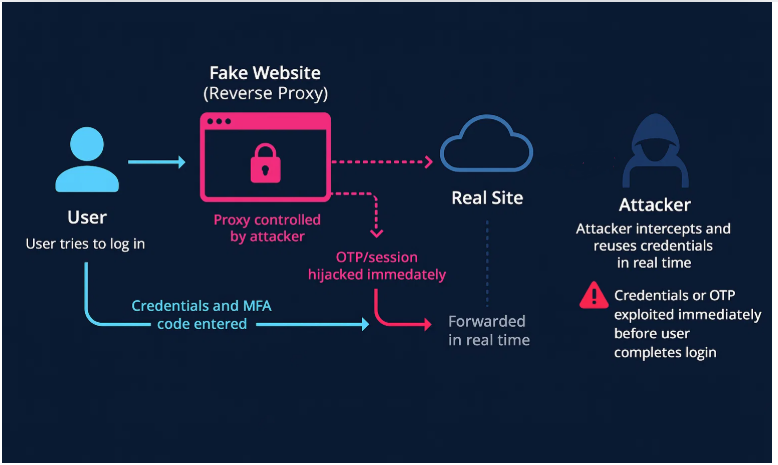
Reverse proxy phishing is a rising form of account takeover phishing that uses real-time credential relays. These phishing proxies are explicitly designed to bypass MFA, allowing attackers to hijack sessions before users even finish logging in. This tactic breaks traditional defenses like MFA and domain detection, making it one of the most dangerous forms of phishing today.
Types of Real-Time Phishing Attacks Using Man-in-the-Middle Techniques
Reverse proxy phishing is just one way attackers use man-in-the-middle techniques to hijack credentials in real time. Another critical category involves network-layer manipulation.
Reverse Proxy Phishing
- The user clicks a link to a fake site with a different URL.
- The site uses a reverse proxy to relay the user’s credentials and MFA code to the real site.
- The attacker logs in before the user, hijacking the session.
Infrastructure-Based Real-Time Phishing
- The user types in the correct URL but lands on a spoofed site that appears legitimate.
- This scenario results from network manipulation like DNS poisoning or Evil Twin Wi-Fi.
Network-layer attacks like DNS poisoning or Evil Twin Wi-Fi are notoriously difficult to detect directly. That’s why Memcyco focuses on identifying the resulting phishing behavior using browser and device-level behavioral signals to spot when users land on spoofed sites, regardless of how they got there.
How Reverse Proxy Phishing Works
To the user, it looks like a normal login. But behind the scenes, a phishing proxy is already intercepting and relaying their credentials in real time. Reverse proxy phishing isn’t hand-coded by elite attackers –it’s industrialized. Turnkey phishing-as-a-service platforms now make it easy for fraudsters to deploy fake login pages that look real, function in real time, and forward credentials to the actual site without raising alarms.
- Victim lands on the fake site, believing it to be real.
- Credentials and MFA codes are entered, as normal.
Proxy server relays these to the real site in real time. - Attacker takes over the session, logging in as the user before MFA expires.
- Account is compromised instantly, often with no visible signs to the user or the organization.
Reverse proxy phishing attacks allow cybercriminals to hijack login sessions in real time by intercepting credentials and MFA codes through a proxy server that relays traffic between the victim and the real site.
Why Traditional Phishing Defenses Fail Against Real-Time Phishing Attacks
Reverse proxy phishing breaks the assumptions behind most phishing protection strategies. It defeats:
- Domain-based detection: Because the proxy uses real-time traffic, phishing sites can mimic legitimate domains closely, even using HTTPS.
- Takedowns: These attacks do their damage within minutes. By the time a takedown is issued, the session is already hijacked.
- MFA: MFA isn’t broken, but it has been bypassed. These kits are designed to capture and relay one-time passcodes before they expire.
Attackers often rely on rogue tools and phishkits like EvilProxy, Frappo, Muraena, and Modlishka to conduct these real-time attacks. The broader trend is part of what Microsoft refers to as Adversary-in-the-Middle (AiTM) phishing. According to Proofpoint and other threat researchers, phishing proxies like EvilProxy were used in over 1 million attempted account takeovers in early 2025, targeting cloud services, finance, and enterprise portals.
How These Attacks Fuel Account Takeover
Reverse proxy phishing dramatically shortens the time between credential theft and account compromise. Once attackers gain real-time access through a phishing proxy, they can:
- Change passwords and recovery settings to lock out the legitimate user
- Access sensitive data, financial records, or customer information
- Initiate fraudulent transactions or trigger refund abuse
- Escalate the breach into broader business email compromise (BEC) or lateral movement across systems
And unlike traditional phishing, users rarely realize what happened until they’re locked out, or the damage is done. There are often no alerts, no logs, and no visible signs that the session has been hijacked – only a silent takeover.
Reverse proxy phishing doesn’t just enable impersonation, it gives attackers everything they need to act as the user in real time, turning a moment of deception into immediate account takeover.
Reverse proxy phishing is hard to detect because it mimics legitimate user activity. Still, there are telltale signs and steps you can take to reduce exposure:
-
Monitor logins from new or untrusted devices
-
Watch for unusual MFA behavior or user complaints about login loops
-
Educate users that HTTPS and padlocks don’t guarantee legitimacy
-
Implement a real-time ATO prevention solution that works in the browser
Key Point: MFA alone is no longer enough when attackers can relay codes in real time.
Remember: A secure-looking padlock doesn’t confirm a site’s authenticity.
Traditional defenses blink. Reverse proxy phishing doesn’t. If your detection isn’t operating at browser speed, you’re already too late.
Why Real-Time Insight Is so Critical to Prevent Reverse Proxy Phishing
Reverse proxy phishing unfolds in seconds, making it nearly impossible to stop once credentials or MFA codes are entered. The attacker uses them in real time, often logging in before the legitimate user even completes authentication. Traditional defenses, like login anomaly monitoring, MFA verification, or phishing domain takedowns – aren’t fast or targeted enough to stop it. Once data is submitted, it’s already compromised. That’s why security teams need browser-level defenses that operate before submission, detecting phishing behaviors in the moment and acting instantly to protect users.
How Memcyco Disrupts Reverse Proxy Phishing in Real-Time
Memcyco doesn’t detect the proxy server itself, but it does identify and disrupt the phishing behaviors that result from reverse proxy tactics, making it possible to intervene before attackers succeed. Here’s how:
Real-Time ‘Nano Defenders’
Part of its secret sauce, Memcyco’s ‘Nano Defenders’ operate at the browser level, detecting in real-time when a user interacts with a live phishing proxy site, before credentials are even stolen.
Decoy Credentials
If a user begins entering credentials on a spoofed proxy site, Memcyco replaces the input with decoy data in real time – rendering it useless to attackers and flagging the phishing behavior in action.
Suspicious Login Pattern Detection
By identifying MitM signals and credential relay patterns across devices, Memcyco detects phishing behaviors that often precede session hijack, giving security teams the chance to act before credentials are abused.
Real-time Victim Identification
Even if the user submits data, Memcyco identifies the victim in real time, enabling proactive intervention before fraud occurs.
Attack Disruption and Deception
Beyond detection, Memcyco automates rapid takedown initiation, also using proactive deception measures to disrupt scammer operations – while enriching your fraud engine with previously unobtainable attack data, for model improvement.
In short, phishing proxies don’t wait, and neither should your defenses. Memcyco identifies and disrupts these attacks in real time, before credentials are ever abused.

Bottom Line: Only Real-Time Defense Stops Real-Time Phishing Attacks
The rise of reverse proxy phishing marks a shift in how cybercriminals steal credentials and bypass protections. Reactive defenses like takedowns and MFA alone can’t stop it, but Memcyco’s real-time digital risk protection layer can.
Get a product tour and discover the analyst-backed Memcyco innovations helping scam-targeted enterprises save millions on incident-related opex.
FAQs About Reverse Proxy Phishing
What is a reverse proxy phishing attack?
A reverse proxy phishing attack is a real-time man-in-the-middle technique where attackers relay traffic between a user and the legitimate website through a proxy server, capturing login credentials and MFA codes to hijack sessions instantly.
How does reverse proxy phishing bypass MFA?
Attackers capture the user’s one-time password or push notification and forward it to the real site before it expires. This allows them to authenticate successfully, even if MFA is in place.
How is reverse proxy phishing different from traditional phishing?
Traditional phishing collects credentials for later use. Reverse proxy phishing uses the credentials in real time, enabling immediate access and making the attack harder to detect or prevent after the fact.
Can Memcyco detect reverse proxy phishing attacks?
Yes. Memcyco detects the phishing behaviors enabled by reverse proxy attacks rather than the proxy infrastructure itself. It uses browser-level detection, decoy data injection, and suspicious login pattern analysis to stop these attacks in real time.
What tools do attackers use for reverse proxy phishing?
Popular kits include EvilProxy, Frappo, Muraena, and Modlishka. These kits automate the creation of fake login sites that act as reverse proxies to legitimate platforms.
Why can’t domain takedowns prevent reverse proxy phishing?
Because the attack executes in real time, often within seconds, by the time a phishing domain is identified and taken down, the damage is already done.