As scam-prone enterprises know, innovations in digital technologies raise the specter of phishing-related brand impersonation scams as much as they help mitigate it. Take rogue Generative AI tools like Fraud GPT and ‘Phishing-as-a-Service’ as just two examples of how fraudsters are co-opting new technologies as part of customer account takeover (ATO) schemes. The net outcome is a paradigm of immaculate, off-the-shelf scams that hide in plain sight, evading the vigilant eye of even your most scam-savvy customers.
The good news is that there are now anti-fraud innovations that act as circuit breakers, proactively disrupting and dismantling the attack anatomy of phishing and impersonation-related scams in real time.
We’ll get to that. First, let’s unpack what scam-targeted enterprises can expect in terms of the evolving cybersecurity trends 2025.
1. Proliferation of AI-Enhanced Social Engineering
2024 was the year in which AI-assisted scams truly exploded. In 2025, with advancements in widely available large language models (LLMs), AI-assisted social engineering schemes targeting customer accounts will grow in both volume and sophistication.
In 2024, Booking.com reported a staggering 900% increase in travel-related scams attributed to AI-generated phishing content. What’s terrifying about this stat is that the damage from travel scams often implicates the broader ecosystem, including airlines for which loyalty program fraud and account takeovers have become as big a problem as payment fraud in the financial sector.
By some estimates, there are now over 30 trillion unspent flyer miles in circulation with hard cash value, according to McKinsey.
Whether you’re a bank, payment provider or airline, what’s certain in 2025 is the need to adopt more proactive strategies capable of pre-empting, revealing, and countering brand cyber attacks at the speed of AI.
2. Bigger Phishing-related Attacks (Online and Offline)
Phishing remains one of the most prevalent and effective cyberattack methods. To put the unrelenting growth into context, phishing emails surged by 1,265% through to Q4 of 2023, following the arrival of ChatGPT, according to email security leader, SlashNext.
With the AI turbo boost we mentioned, phishing is now a highly tailored and targeted phenomenon. What’s worse? Phishing-related attacks are no longer confined to the digital sphere. QR phishing (also known as QRishing) is taking phishing offline and into physical spaces. Next time you scan a QR code to pay for parking or a burger and fries, be wary. Fraudsters increasingly replace legit QR codes in public spaces with malicious QR codes that quietly redirect victims to phishing sites, leading to credential theft, ATO and payment fraud.
Needless to say, the insidious nature of QRishing lies in its ability to circumvent customer vigilance. If there’s no link to click, why be suspicious, right?
3. Booming Social Media Brand Impersonation Scams
Social media is becoming one of the most dangerous fronts in the battle against brand impersonation, and this trend is set to reach new heights in 2025. Scammers increasingly exploit platforms like Instagram, Facebook, and LinkedIn to create fake profiles, ads, and posts that deceive users into handing over sensitive information or making fraudulent transactions. According to the Global Anti-Scam Alliance, over $1.03 trillion was lost to scams in 2024, with a significant share linked to social media fraud.
One alarming trend involves generative AI being used to create highly convincing fake ads and profiles. For instance, scammers can deploy AI-generated images and videos to mimic a brand’s look and feel, ensuring their fraudulent schemes go undetected by even the savviest consumers. Expect to see more of this as part of cybersecurity trends 2025.

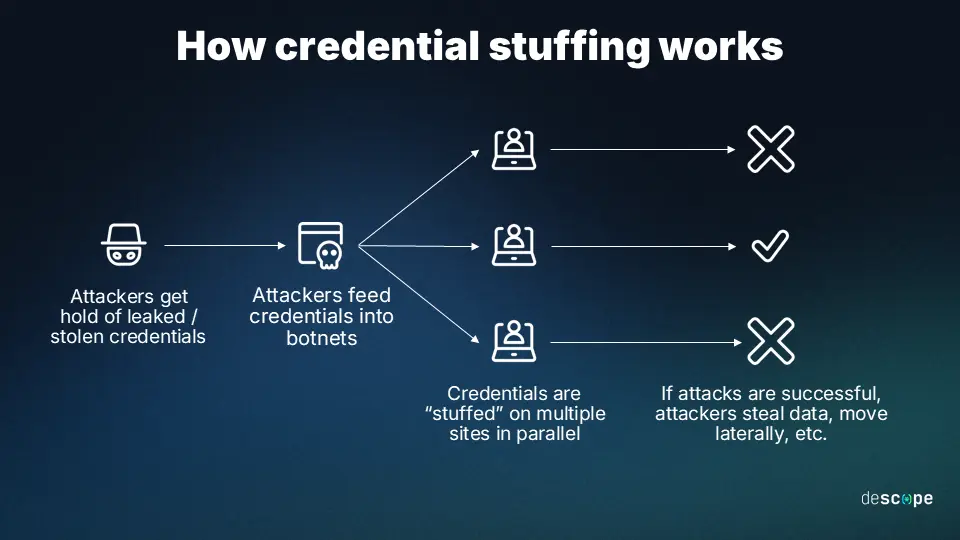
4. Expect a Surge in Credential Stuffing and Customer ATO
With cybercriminals increasingly adept at bypassing authentication methods, account takeover (ATO) attacks will continue to rise in 2025. Compromised credentials and credential stuffing – a key driver of ATOs – now accounts for billions of fraudulent login attempts annually, affecting industries from eCommerce to financial services.
To stop credential stuffing, enterprises prone to such attacks need to pivot away from server-based credential stuffing detection to browser-based detection. By doing so, it’s possible to detect not just successful login attempts, but failed attempts also, increasing both the speed and accuracy of credential stuffing attacks.
What makes modern customer ATOs particularly concerning is the fact that attackers can now bypass even the most trusted security measures. Techniques like MFA fatigue attacks – where users are bombarded with authentication prompts until they mistakenly grant access – and vulnerabilities in FIDO2 passkeys create moments of opportunity for attackers.
5. Hard-to-Detect Bots and Financial Fraud Tactics
As mentioned (you’re probably tired of hearing it) AI is bootstrapping fraud schemes for speed and scale. In 2025, expect the use of bots and generative AI to grow. Expect also the fact that these tactics help fraudsters bypass traditional detection tools, creating a growing need for pre-emptive, real-time solutions for fraud teams.
What’s powerful about such solutions is their ability to dismantle and disrupt scams at the point of impact, reducing reliance on customer vigilance. No matter how many scams customers fall for, pre-emptive, real-time solutions like Memcyco secure credentials and card data, slashing incident-related expenses while actively exposing attackers and identifying victims.
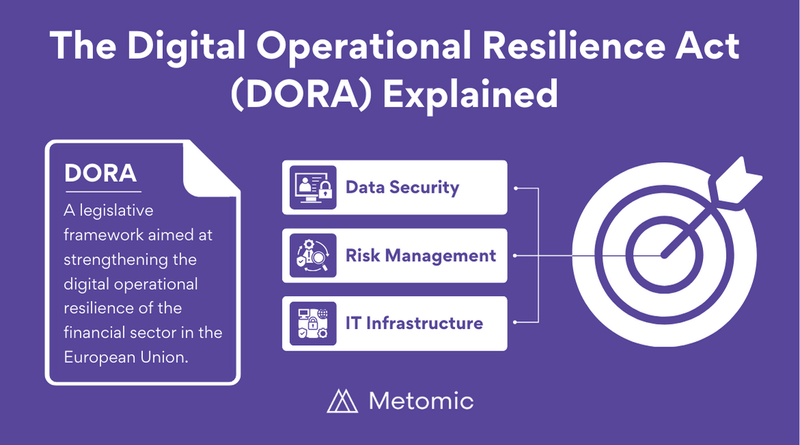
6. Tighter Digital Operations Resiliency Regulation
If you haven’t heard of the EU’s The Digital Operational Resilience Act (DORA) that became law on January 17th, you will. Perhaps when it’s too late. It represents a pivotal shift in how financial institutions with EU operations approach cybersecurity and operational resilience.
DORA mandates stringent requirements for incident detection, risk management, and operational continuity. While focused on the EU, its influence extends globally, as businesses outside the region that interact with EU financial institutions may need to comply.
Memcyco contributes to DORA compliance readiness by equipping businesses with real-time incident detection, mitigation and reporting tools. Its advanced capabilities ensure organizations can meet DORA’s demands for proactive risk management while safeguarding customer data and maintaining operational continuity.
How to Get Ahead of these Cybersecurity Trends in 2025
What will be critical in 2025 for enterprises prone to digital impersonation scams is a rapid pivot from reactive, to proactive strategy. To achieve that quickly, Memcyco’s agentless, real-time technology installs easily in your website code, activating proactive protection from the 2025 threats discussed.
Real-Time Digital Impersonation and Customer ATO Protection
Unlike traditional solutions that rely on intermittent scanning, Memcyco immediately flags impersonation attempts and attacks from their inception, and as they evolve in real time. In this way, Memcyco elevates and amplifies digital trust, pre-emptively flagging brand scams before they hit your customers, right from the attack preparation phase. Once scams are live, Memcyco shields card data and credentials no matter how many scams customers fall for.
Advanced Device Fingerprinting and Analytics
Unlike most device fingerprinting solutions, Memcyco’s advanced device fingerprinting assigns truly unique identifiers to each device, preventing overlaps in device identification that result in false positives and negatives. More than that, advanced device fingerprinting enables implicit trust of legitimate users. Instead of the usual multi-factor authentication (MFA) friction, and challenging users with suspicious login verification, Memcyco locks out attackers from your legitimate site, while allowing users continual, frictionless account access from trusted devices.
Meanwhile, suspicious devices, or devices used as part of attacks are automatically blocked. By integrating advanced device fingerprinting as part of a more proactive strategy, scam-prone enterprises can elevate phishing and impersonation-related fraud detection and prevention, while actually elevating frictionless experience.
AI-Powered Detection of Phishing Sites not in Threat Databases
Memcyco leverages proprietary AI models and semantic analysis, flagging phishing sites not yet listed in threat databases. Memcyco’s AI capabilities also detect low reputation referrals (also known as redirects) that send scam victims from fake phishing sites back to your original site. Fraudsters often deploy this tactic to cover their tracks by minimizing the victim’s time spent on the fake site and avoid rousing user suspicion.
Real-time Credential and Card Data Theft Protection
Real-time credential and card data theft protection, powered by Memcyco’s decoy data capability, offers businesses a proactive shield against phishing and impersonation scams. By strategically deploying fake credentials or card data, Memcyco misdirects attackers and prevents them from accessing real customer information. This approach not only neutralizes threats but also provides valuable forensic insights, helping organizations trace attack patterns and identify malicious actors.
This capability transforms the defensive landscape by turning attempted attacks into opportunities to gather intelligence while safeguarding sensitive data. Businesses benefit from reduced financial losses, improved regulatory compliance, and strengthened trust among customers, knowing their data is protected by proactive, decoy-driven security measures.
Take the Next Step: Get a Tailored Product Tour
This is the part where we ask you to click ‘Contact us’ and book your product tour. You’ll lear exactly how Memcyco’s agentless, real-time technology is helping scam-prone enterprises save millions annually in impersonation scam and phishing-related expenses.
During your product tour, you’ll explain to us your specific challenges and we’ll explain in detail how Memcyco performs in each scenario.