In industries like banking, e-commerce, and logistics, where millions of transactions occur daily, fraud often begins with a single malicious device. Attackers use proxies and VPNs to mimic legitimate users, but subtle clues — browser settings, session habits, or time zone mismatches – can expose their schemes.
Device fingerprinting solutions have become essential for businesses aiming to enhance fraud prevention and improve user experience. These tools analyze unique device attributes to identify and track devices, ensuring security and compliance with data privacy regulations. In this post, we review the top device fingerprinting solutions available, exploring their features and use cases.
What are Device Fingerprinting Solutions?
Device fingerprinting solutions are advanced fraud detection tools that create a unique identifier, or “fingerprint,” for each device interacting with your digital systems. These tools differentiate legitimate users from fraudsters by analyzing hardware, software, user activity, and behavioral attributes, even when bad actors use tools like proxies or VPNs to mask their identities.
Device fingerprinting identifies and tracks devices based on unique characteristics like browser configurations, installed plugins, and hardware settings. This technology is critical for online banking and e-commerce fraud prevention, enabling businesses to recognize devices while adhering to privacy regulations like GDPR.
How Device Fingerprinting Works
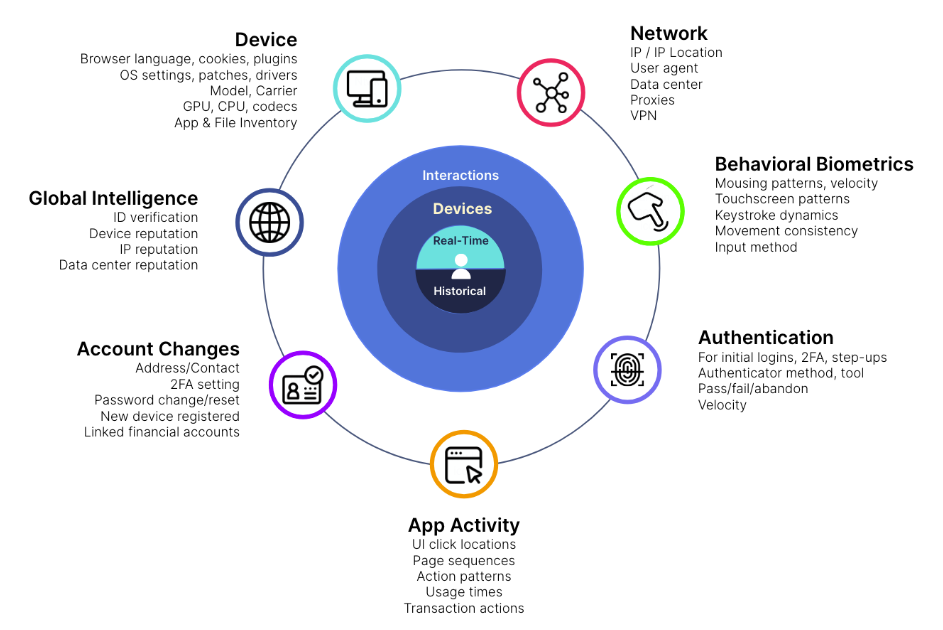
At the core of device fingerprinting is the ability to analyze and correlate data from multiple device attributes in real-time. When a user interacts with your application or website, the solution collects and processes non-intrusive data elements like browser plugins, screen resolution, operating system, time zone, and even behavioral metrics like typing speed or click patterns. Tools then hash the data into a unique identifier consistent across sessions, even if the user’s IP address or cookies change.
These solutions flag potential fraud by comparing this identifier to known fingerprints and analyzing anomalies and inconsistencies. For example, a mismatch between the declared location and time zone could indicate using a proxy or VPN. Similarly, rapid sequential login attempts across multiple accounts from the same device fingerprint could signal credential stuffing attempts.
Device fingerprinting solutions collect non-personally identifiable information (non-PII) to respect privacy regulations while ensuring robust fraud detection. Key data points include:
- Hardware attributes: Processor type, GPU, screen resolution, battery status, and device orientation.
- Software details: Browser type, installed plugins, user-agent string, and operating system version.
- Network characteristics: IP address, DNS settings, and proxy/VPN detection.
- Behavioral patterns: Typing cadence, mouse movements, touch gestures, and session duration.
This granular data enables fingerprinting solutions to identify unique devices with remarkable accuracy while keeping your business compliant with SOC 2, GDPR, CCPA, and other essential data privacy regulations.
Integrating Device Fingerprinting Into Your Security Plan
Industries with high transaction volumes, like banking and e-commerce, benefit most from device fingerprinting solutions. Security teams can leverage them to prevent account takeovers (ATOs), detect bot-driven attacks, and flag anomalous behavior in real-time. Additionally, device fingerprinting can enrich fraud analytics, providing deeper insights into attacker behavior and enabling proactive adjustments to your security posture.
The strategic integration of device fingerprinting tools is about more than just detecting fraud – it extends to creating a seamless, adaptive security framework. These solutions can be a dynamic layer in your risk-based authentication (RBA) strategy. By assigning risk scores to devices based on fingerprinting data, you can dynamically escalate security measures, such as triggering multi-factor authentication (MFA) or blocking high-risk sessions entirely. For example, if a device previously associated with malicious activity attempts to log in, fingerprinting ensures the system responds immediately with additional scrutiny or access denial.
Device fingerprinting also helps minimize false positives, a persistent challenge in traditional fraud detection systems. By correlating fingerprints with behavioral analytics and historical data, you can refine decision-making and improve accuracy in detecting genuine threats.
False positives are minimized without disrupting legitimate user activity, critical for maintaining a seamless customer experience.
Why You Need Device Fingerprinting Solutions
Fraudsters mimic “white” devices to slip past defenses, using techniques like session hijacking, device spoofing, and rapid proxy rotation. They manipulate browser configurations, disguise geolocations, and mask time zones to blend in with genuine traffic. This level of deception targets blind spots in existing security toolkits.
Device fingerprinting tools expose these tactics by analyzing a device’s unique attributes, such as hardware configurations, software environments, and behavioral patterns, and detecting inconsistencies that reveal fraud, even when proxies and spoofing tools are in play.
Some types of attacks and risks these solutions help you mitigate include:
Identity Theft
Attackers often use stolen credentials and spoofed devices to gain unauthorized access. Device fingerprinting prevents this by flagging inconsistencies between a user’s known device profile and a new login attempt.
Account Takeover (ATO)
In account takeovers, attackers use stolen credentials to infiltrate user accounts and conduct unauthorized transactions. Device fingerprinting identifies repeated login attempts, rapid session switching, or other suspicious patterns across multiple accounts for immediate countermeasures.
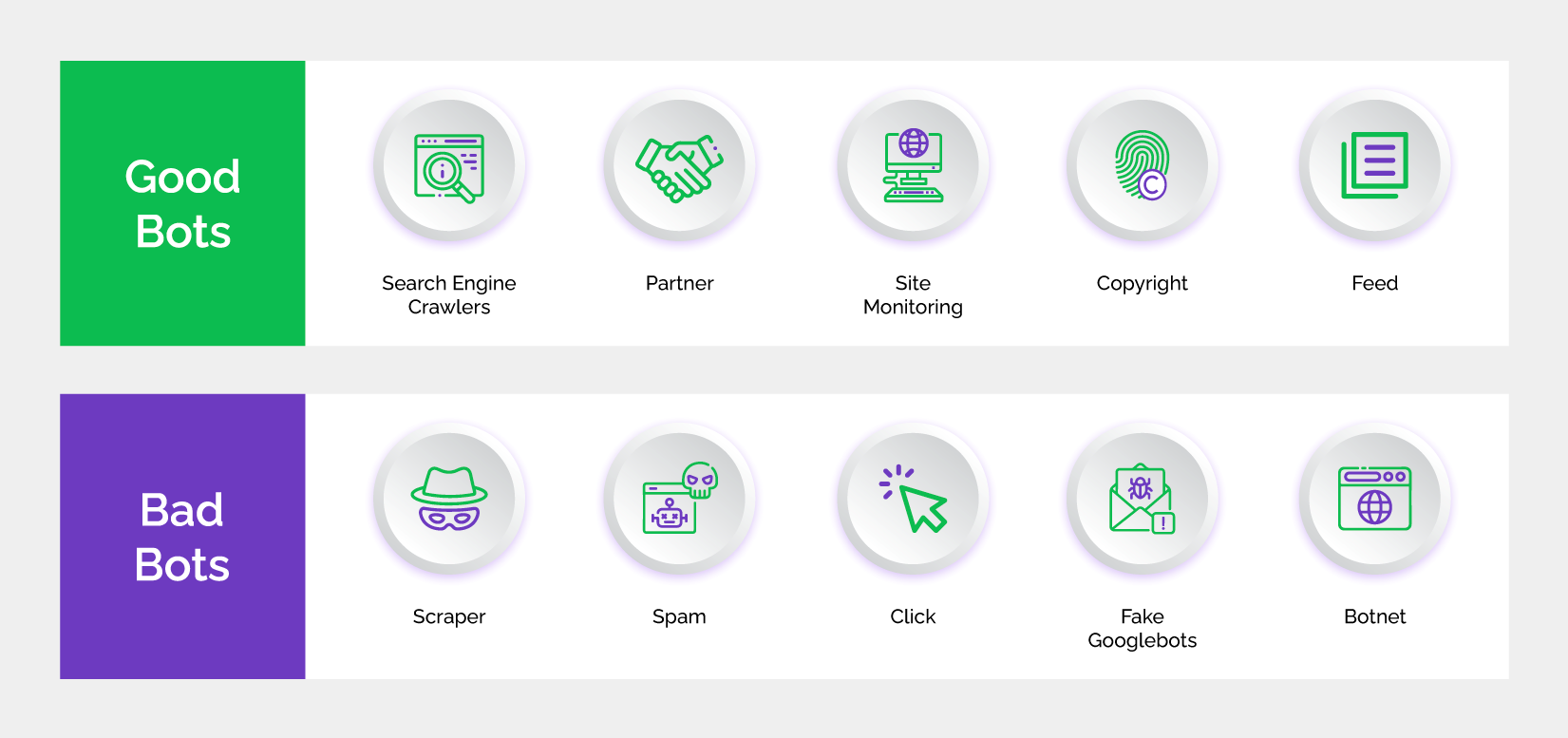
Bot Attacks
Automated bots attempt to execute credential stuffing, checkout fraud, or fake account creation. Fingerprinting tools analyze subtle device details like mouse movement, click behavior, and plugin configurations that bots can’t replicate to help you differentiate bots from genuine users.
Account Sharing and Abuse
Shared login credentials across multiple devices can violate usage policies, particularly for subscription services. Device fingerprinting monitors consistent device use and flags accounts accessed from unrelated or suspicious devices, ensuring compliance and protecting your revenue streams.
Fake Websites
Fraudsters use fake websites to steal user credentials. Device fingerprinting embedded within legitimate sites tracks interactions from compromised devices or phishing links and issues real-time alerts to prevent credential theft and identify spoofed domains.
Key Features to Look For in Device Fingerprinting Solutions
Device fingerprinting solutions differ in capabilities, but the most effective tools share key features that address modern fraud challenges. From identifying suspicious behaviors to integrating seamlessly into your existing security infrastructure, prioritizing these features ensures your chosen solution(s) deliver maximum value.
1. Behavioral Tracking
Sophisticated fraud often hides behind legitimate devices, but behavioral patterns can help counter that, by offering consistent and reliable indicators of fraudulent activity. Behavioral tracking analyzes how users interact with your platform – such as typing speed, mouse movement, or swipe patterns – to identify anomalies that static identifiers can’t catch. For example, a bot attempting credential stuffing may mimic login credentials perfectly, but its rapid, repetitive actions reveal its true nature. Look for solutions beyond device data and include behavioral insights to catch fraudsters who have already bypassed other defenses.
2. Cross-Device Recognition
Fraudsters regularly switch devices to evade detection, but a strong fingerprinting solution ensures that identity is related to the user, and not just to the device. Cross-device recognition identifies and tracks user sessions across multiple devices by analyzing unique device and user signatures, to create a unified view of user behavior. This feature is critical for preventing sophisticated attacks like account takeover, where fraudsters test credentials on multiple platforms. It also helps detect and disrupt credential sharing or abuse across devices.
3. Real-Time Monitoring
Fraud attempts happen in seconds, leaving little room for delayed responses. Real-time monitoring pinpoints suspicious activity as it unfolds, allowing immediate action to disrupt potential attacks. For instance, if a device begins logging into multiple accounts within seconds or accesses resources from high-risk geolocation, the system can block the session, trigger additional authentication, or alert security teams. Fraudsters can exploit the delay to execute account takeovers, steal data, or commit unauthorized transactions without this feature.
Top 8 Device Fingerprinting Solutions
1. Castle
Castle’s device fingerprinting solution is designed to deliver real-time, risk-based insights by analyzing detailed device attributes and behaviors. What sets Castle apart is its emphasis on contextual anomaly detection. The platform continuously evaluates device activity against historical patterns, flagging unexpected behaviors like sudden changes in geolocation, unusual device setups, or deviations in session duration.
Its Integration with APIs and developer-friendly SDKs makes it adaptable to environments, enabling businesses to embed device intelligence into custom workflows and security architectures.
Best for
Organizations that need developer-friendly solutions to integrate device fingerprinting into custom fraud detection workflows.
What customers say
“The solution is easily deployed and easy to maintain. The Castle team is fantastic to work with and typically responds to questions within an hour, which is incredible.”
2. Memcyco
Known for its focus on digital impersonation prevention, Memcyco leverages device fingerprinting in combination with its unique Nano Defender technology, to protect businesses from phishing and account takeover fraud. It offers seamless integration with existing fraud detection systems, ensuring accurate and scalable protection.
Memcyco combines unique device identification, real-time anomaly detection, and extended identity profiling to provide precise and effective protection against account takeover (ATO) and credential-based fraud.
Each device is assigned a truly unique ID, eliminating the risk of duplicate or overlapping identifiers. This approach doubles detection accuracy, enabling the identification of malicious devices without disrupting legitimate users.
Memcyco also tracks device history and builds a comprehensive interaction profile across sessions. This allows it to identify anomalies, such as unusual login times, unexpected geolocations, or behavior patterns that deviate from the norm.
Lastly, Memcyco makes sure to track separately devices and users, assuming that in many cases they cannot be directly associated with each other – which provides extra accuracy to the analysis.
Best for
Enterprises and medium-sized businesses prioritizing precision-driven ATO prevention and real-time fraud mitigation.
What customers say
“ It is an amazing, continuously improved product that addresses a significant problem in our digital society. A key pro is the ability to alert users when a scam targets them without requiring them to install anything. Even if they ignore the alerts, the solution has ways to keep protecting them.”
3. TrustDecision

TrustDecision uses advanced machine learning and comprehensive device analysis to detect fraud. Its integration with real-time fraud scoring allows businesses to act immediately on high-risk devices while ensuring minimal disruption for legitimate users. The platform also excels in scalability, making it suitable for handling high transaction volumes or complex, multi-regional operations.
Best for
Enterprises handling high transaction volumes and requiring scalable solutions.
What customers say
“TrustDecision, with its professional and high-quality services and capabilities, has effectively helped us reduce the risks of mass registrations and credit card fraud. They are a reliable partner in our cross-border expansion efforts!”
4. RISK IDENT
Risk Ident’s device fingerprinting technology captures and analyzes a broad spectrum of device attributes to create persistent, tamper-proof device profiles. Its ability to detect fraud patterns over time through self-learning algorithms that correlate device data with historical fraud cases is handy.
The solution integrates seamlessly with case management systems, enabling your security teams to access enriched device intelligence for faster, data-driven decision-making. Additionally, Risk Ident offers pre-built and customizable fraud prevention workflows.
Best for
Businesses in high-risk sectors like banking and insurance need persistent, data-enriched device intelligence to identify and mitigate complex fraud patterns.
What customers say
“The e-commerce solution is straightforward to use. It will help you to find connections between orders you would not see. Were there fraud orders already sent to this address or nearby? Did you already have fraud orders from this device or a device, etc.”
5. IPQS
IPQS is a versatile device fingerprinting solution with some nifty features. A standout feature of IPQS is its proxy and VPN detection, which accurately identifies high-risk traffic masked by anonymization tools. Additionally, it leverages machine learning to assign risk scores to devices, flagging activities like account creation fraud, fake signups, and bot-driven attacks. The platform’s real-time API integrations allow seamless integration into authentication workflows, enabling adaptive security measures based on device behavior.
Best for
Companies looking to enhance fraud prevention through advanced proxy/VPN detection and real-time integrations for adaptive security in fast-paced digital environments.
What customers say
“IPQS provides a lot of information that I may use to improve my security decisions, and though there haven’t been fraudulent (transactions) lately, the fraud score tool looks at behavior over a long period to stop the usage of malicious IP addresses. Furthermore, the program’s simple interface helps me… accelerate risk assessment procedures.”
6. HUMAN Security

HUMAN Security’s device fingerprinting solution protects against large-scale bot attacks, fraud, and malicious automation. It detects bots that try to mimic human behavior using advanced behavioral analysis and machine learning. The system processes billions of interactions daily to spot threats like session hijacking, credential stuffing, and fake account creation. HUMAN also works smoothly with fraud detection and ad integrity tools, making it easy to strengthen your security across platforms.
Best for
Enterprises facing large-scale bot attacks and malicious automation.
What customers say
“Integrating with HUMAN has allowed us to focus more on building our platform and less on mitigating fraud. We’re incredibly grateful for the time and resources HUMAN saves us daily.”
7. Kount
Kount’s solution combines device data with its proprietary Identity Trust Global Network, which analyzes billions of interactions across industries to detect anomalies and identify high-risk devices. Kount also excels in adaptive fraud prevention, providing dynamic risk assessments that adjust based on real-time device behavior, geolocation inconsistencies, or session anomalies.
Best for
Companies seeking an integrated fraud prevention platform with global intelligence.
What customers say
“Kount can be used in several versatile and complex ways that allow for customized use by any business. They have utilized their own AI learning and partnered with several companies to allow integrations into their systems in every facet of fraud.”
8. TruValidate
TruValidate by TransUnion delivers device fingerprinting as part of its comprehensive identity and fraud prevention platform to provide precise and actionable insights. TruValidate enhances fingerprinting capabilities by correlating device intelligence with behavioral and transactional data. Its global identity network aggregates billions of anonymized transactions to provide deep context for evaluating device and user behavior. The platform integrates seamlessly with multi-layered fraud prevention strategies, with adaptive authentication workflows and scoring.
Best for
Businesses wanting a globally informed device fingerprinting solution integrated into a multi-layered identity and fraud prevention strategy.
What customers say
“The best thing I like about TruValidate is that it helps in analyzing and finding fraud patterns that can mislead Customers or Clients with wrong information or misrepresentation of the organization.”
Turn User Device Data into Fraud Prevention
Attackers are constantly finding new ways to commit digital fraud, using malicious devices, stolen credentials, VPNs, bots, etc.. Device fingerprinting helps stop these threats by analyzing how devices behave, not just identifying them. It spots suspicious patterns, like unusual logins or mismatched device data, so your security team can detect and block fraud early. By connecting these clues across devices and users, device fingerprinting turns fraud detection into a proactive, intelligence-driven process.
Memcyco takes this intelligence a step further. Its advanced device fingerprinting capabilities, unique device IDs, detailed history tracking, and extended identity profiles provide the real-time action required to stop digital impersonation and account takeover fraud before they escalate. Memcyco’s solution combines that unique device fingerprinting technology with its Nano Defender fake site identification mechanism to provide a novel approach to dealing with digital impersonation and ATO fraud.
Memcyco’s solutions integrate seamlessly into existing workflows so you can build a fraud prevention strategy that protects your systems and customers. Discover how Memcyco’s real-time digital risk protection can give your organization the edge against evolving fraud tactics.
Learn more or contact us today.