With the exponential expansion of AI, bad actors are frothing at the mouth. Advanced technology for automating social engineering techniques that previously required technical know-how is now within arm’s reach of anyone with a keyboard. Attempts to exploit and deceive are more common than ever, and they are emptying business’s pockets.
In 2023, 800 businesses worldwide reported fraud losses totaling 6.5% of their revenue, amounting to $359 billion. In the US alone, losses to the businesses surveyed reached 6.7% of revenue, totaling $112 billion. Projected globally, this figure would expand by orders of magnitude.
With high gains and plentiful potential victims, credit bureaus are an irresistible target, with companies like TransUnion taking hit after hit. So, what scams affect credit companies like TransUnion, and how can you protect your business?
What is the TransUnion Scam?
While there isn’t one specific “TransUnion scam,” the term often refers to fraudulent activities targeting or involving TransUnion. As one of the leading credit bureaus in the world, TransUnion provides credit ratings to millions of customers, helping companies assess credit risk accurately.
Recently, the company has been particularly targeted by digital scams, including identity theft, phishing, smishing, and account takeover (ATOs). Large-scale phishing attacks targeting TransUnion customers are so prevalent that multiple Reddit chats are dedicated to discussing them. In these chats, users ask about the legibility of specific TransUnion communications or share their “almost got scammed” experiences.
Customers are the direct target, as attackers aim to steal their confidential information to obtain fraudulent loans and other financial gains. However, while customers may lose hard-earned cash or see their credit score decline, companies are also significantly impacted. Credit bureaus incur the expense of investigations, possible reimbursement, and reputational damage.
Like all financial services companies, credit bureaus constantly monitor for scams like identity theft, phishing, smishing, and ATOs. These attacks aim to acquire confidential customer information that can later be used to obtain fraudulent loans and other financial gains.
Types of Scams Affecting TransUnion Customers
Though TransUnion is often targeted, the scam methods below are used across credit bureaus and other financial institutions (scammers aren’t brand loyal!).
1. Fake Credit Monitoring Services
Credit bureaus offer customers a monitoring service to track their spending, inform them of changes in their credit rating, and alert them to possible fraud. Scammers establish fake credit monitoring sites that trick customers into entering personal and financial information.
So widespread is the phenomenon that the US Federal Trade Commission (FTC) issued an alert to consumers advising them to be aware of unsolicited emails and smishing (phishing via SMS) offers of credit reports at reduced cost.
2. Identity Theft
Identity theft originates from illicitly procuring personal information like social security numbers, credit card details, or passwords. The data is then used to open fraudulent accounts with lenders or make unauthorized purchases or bank transfers. In this case, the clients of credit bureaus are the primary victims, but the lenders will also have to
3. Synthetic Identity Fraud
This type of fraud involves using synthetic identities that combine actual consumer data (gathered from the dark web or security breaches) with false information. For example, scammers may create a synthetic identity by attaching a valid social security number to a false name and email address. They then use this semi-fake profile to open a new account with the lender and make loan applications.
Lender exposure to synthetic identity fraud is increasing. For US auto loans, bank credit cards, retail credit cards, and unsecured personal loans, the cost of this exposure reached an all-time high of $3.2 billion during the first half of 2024, a rise of 18% yearly.
4. Phishing and Social Engineering
These are deceptive emails, messages, and advertisements that drive people to a fake website (usually looking precisely like their credit provider’s, be it TransUnion or another). Thinking they are visiting a legitimate site, targets may provide sensitive information like passwords or banking details.
Attackers craft all user communications carefully to urge customers to take action. For example, fraudsters may warn customers that their bank account has been compromised or that their credit card was used to get a loan to exploit fear. These techniques work well on people who are less tech-savvy, under stress, or often attention-drifting.
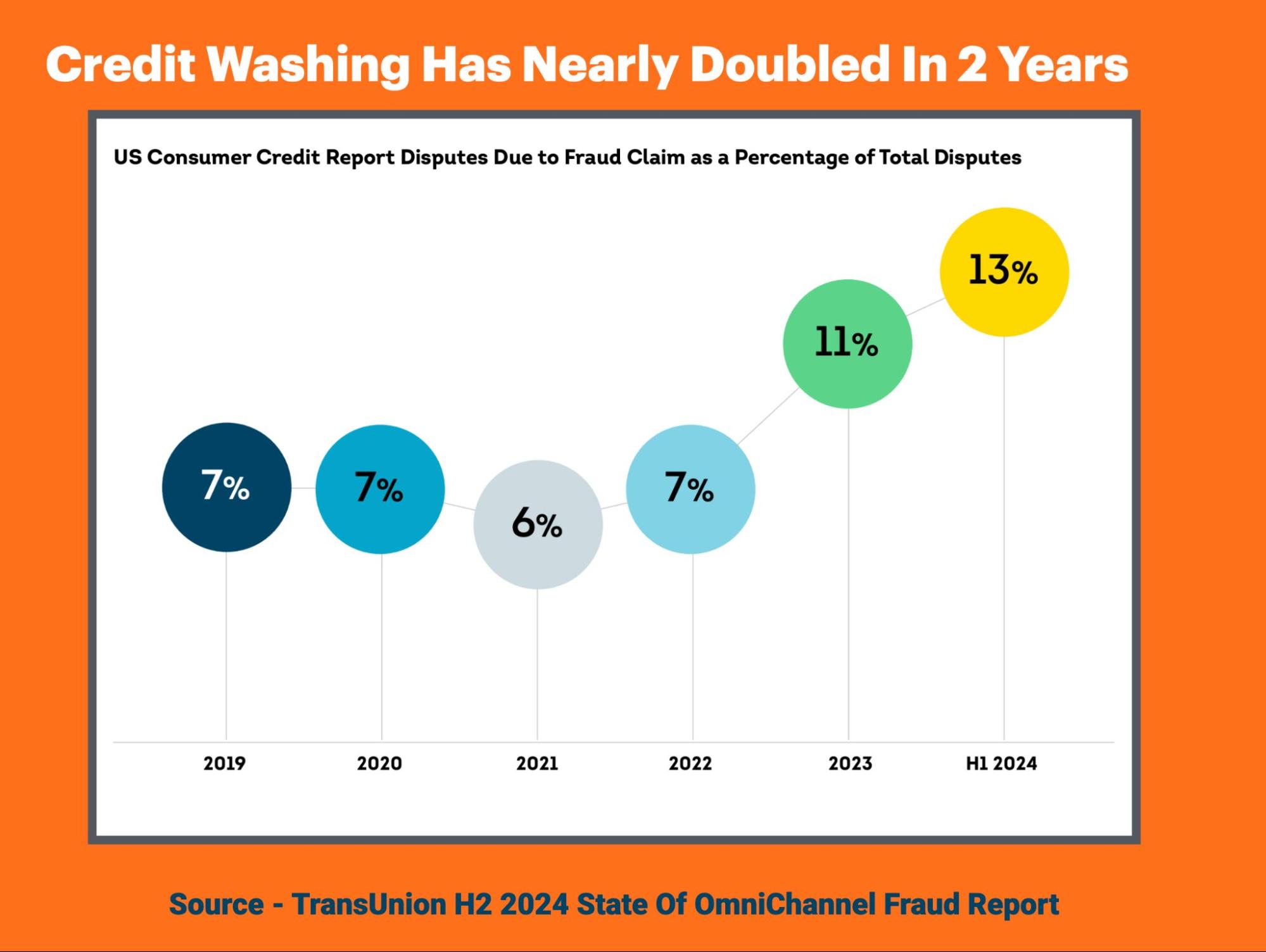
5. Credit Washing
Credit washing happens when fraudsters falsely claim they have been victims of identity theft and ask to remove legitimate negative information from their credit profiles. Exploiting consumer protection laws such as the Fair Credit Reporting Act, they may dispute accurate information on their credit files. This distorts creditworthiness, enabling the “washer” to obtain loans or credit for which they do not legitimately qualify.
6. Loan Stacking Fraud
Loan stacking fraud happens when a dishonest borrower receives multiple loans from different lenders simultaneously. They exploit time delays in lender communication or credit reporting to secure funds they know they cannot repay. This fraud doesn’t only affect credit bureaus and financial institutions but also insurance providers, as fraudulent claims and misrepresented creditworthiness can bleed into policy underwriting, leading to inaccurate premiums and inflated insurance costs.
5 ways to Protect Your Customers from TransUnion-like Scams
1. AI-Driven Anomaly Detection
AI-driven anomaly detection has become central to fraud detection. These anomaly detection tools are based on advanced machine learning (ML) algorithms that analyze vast datasets and discern typical behavior patterns. The data points tracked may include transaction amounts, geographic locations, access times, and other account activities.
They then leverage AI to analyze unusual and unexpected patterns, like simultaneous logins from distant locations, unusually large transactions, or a surge in activity. By flagging such anomalies, they help credit bureaus identify illicit behavior within their systems. The systems work in real-time, and help predict risks, leading to better decision-making. By automating this workflow, personnel are also freed up for other tasks.
2. APIs for Easy Customer Account Freezing
Credit freezing allows customers to lock their credit file, making it inaccessible to creditors or lenders conducting credit checks to approve new credit applications. By restricting account access, customers can protect themselves against identity theft and prevent the creation of fake accounts and loan applications under their names. In some jurisdictions, a credit freeze option is mandatory to comply with legal requirements for digital fraud prevention.
Integrating credit freeze APIs helps improve customer-initiated security. APIs enable real-time communication between credit bureaus and third-party applications and allow users to implement freezes directly from mobile apps, online banking platforms, or customer portals.
A credit freeze is advisable when there is suspected identity theft, after a data breach, or during major life events like moving or the birth of a child. The fact that this functionality is one click away encourages customers to use it more often and take control of their security.
3. Educate Customers to Protect Themselves
Most scams stem from user mistakes, such as inadvertently sharing sensitive information. Making customers aware of exploits and fraudulent behaviors is a powerful tool to prevent confidential data leakage.
Education can take the form of user-friendly guides, videos, and even engaging quizzes. Monthly newsletters or emails with tips keep users informed about evolving threats. Credit bureaus can also partner with other stakeholders to develop comprehensive training materials.
These materials should cover current and emerging threats and remind customers of safe online behavior. For example, they should inform customers about identifying standard phishing techniques like deceptive emails, fake login pages, and urgent messages requesting account details. Proper training enables them to spot scams before they fall victim.
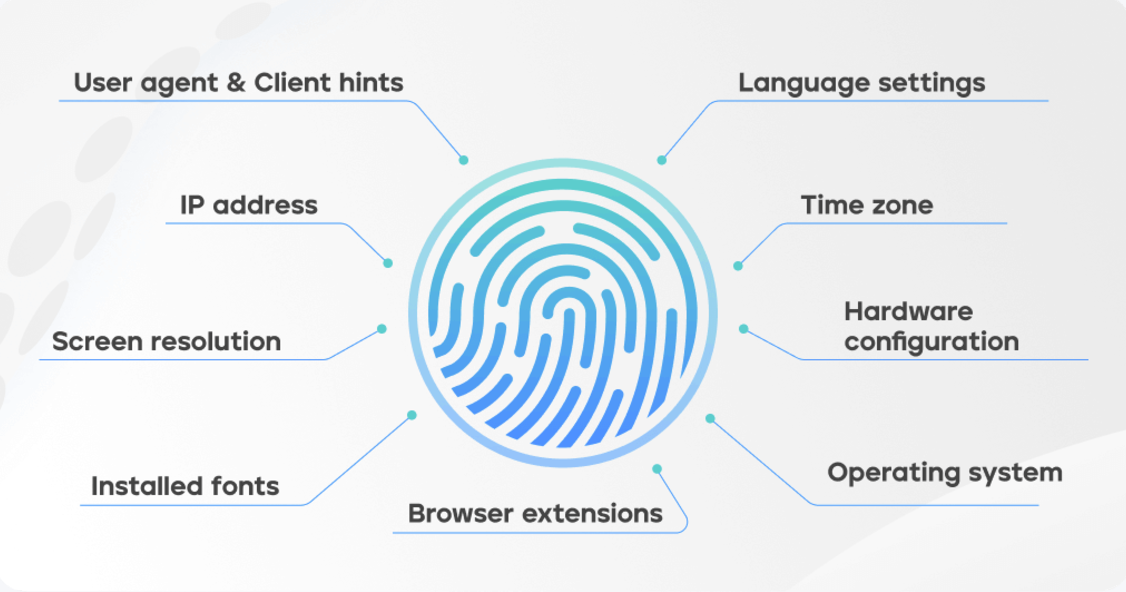
4. Digital Fingerprinting
Digital fingerprinting captures unique identifiers from connected devices and online behaviors. Digital device fingerprinting solutions will automatically collate each device’s “fingerprint” and compare it with the legitimate device credentials of credit bureaus’ customers (each credit bureau should have this updated database). If a suspicious device attempts to log in, it raises a flag for further verification.
Browser type, operating system, time zone, installed plugins, IP address, and even screen resolution are types of fingerprinting data. This information is relatively difficult to conceal, providing a robust and persistent identification method. Beyond static data, companies can also use dynamic behavioral patterns—like typing speed, mouse movements, and browsing habits—to detect suspicious activity.
Credit bureaus can more effectively detect possible fraud by analyzing device attributes and behaviors. Operating in the background, digital fingerprinting can be integrated with application security testing frameworks, ensuring that vulnerabilities are addressed without disrupting the user experience. Importantly, it allows credit bureaus to detect anomalies instantly, enabling swift action to block fraud.
5. Enhanced Authentication Methods
Robust authentication is a very effective layer of protection, ensuring that extra factors can prevent access even if a password is compromised. Types of enhanced authentication include:
- Multi-factor authentication (MFA) combines two or more verification factors -something the user knows (password), something they have (security token or smartphone), or something they are (biometric data like fingerprints or facial recognition).
- Biometric Authentication uses unique identifiers such as facial recognition, iris scanning, and fingerprints.
- Behavioral Biometrics analyze user behavior, such as typing speed, mouse movements, or navigation patterns. This method operates unobtrusively in the background.
- One-time Passwords (OTPs) and Push Notifications can be sent via SMS or email after the initial login has commenced.
- Passwordless Authentication uses unique links, QR codes, or authentication apps to verify identity. It is more secure than traditional passwords.
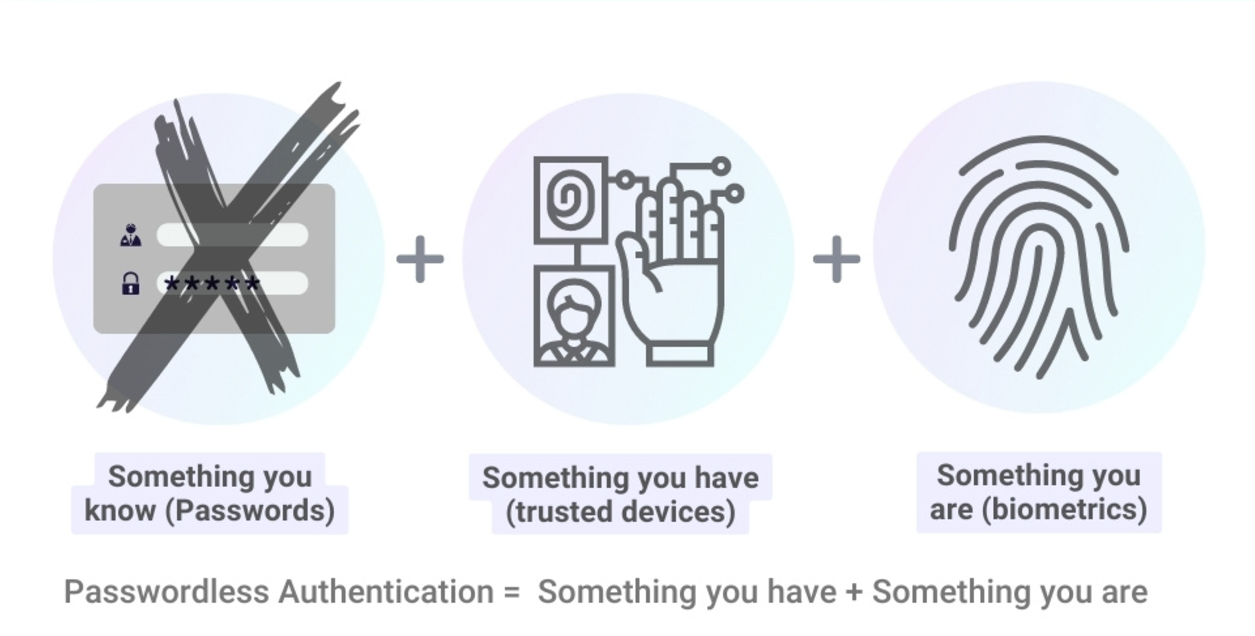
In many cases, enhanced authentication is a requirement for businesses to comply with data protection regulations such as GDPR and CCPA.
Fighting Credit Fraud with Advanced Tools
Credit bureaus are prime targets of fraud—not just within the finance sector but across all industries. With advanced technologies, fraudsters can now execute schemes ranging from basic tactics like phishing to more advanced ones like synthetic identities and credit washing. The world is their oyster.
As a leading provider of real-time phishing and ATO protection, Memcyco deeply understands the threats credit bureaus (and, consequently, their customers) face.
Unlike slower techniques for detecting and neutralizing fake sites, Memcyco’s nano-defender technology detects cloned websites from the moment they go live without the need to wait for intermittent scans that cause delays and create blind spots. Memcyco’s solution also reveals details about the attack, the attacker, and each victim so credit bureaus can act quickly, only intervening and contacting affected customers.
Even when unsuspecting customers submit sensitive data to the fake website, Memcyco’s decoy data capability works behind the scenes to protect them. It instantly replaces customers’ data with artificial, trackable dummy credentials, rendering the stolen data useless to attackers while allowing the credit bureau to gather detailed forensic information about the fraud attempt.
Using this highly advanced technology, Memcyco detects, protects, and disrupts attacks as they unfold, protecting credit bureaus from financial and reputational loss. See how it works.



















