What if there were a way to negate the effectiveness of multi-factor authentication (or even bypass secure login protocols) without ever cracking a password? Session hijacking offers attackers a tempting shortcut to user accounts, bypassing the usual security barriers.
In 2022 alone, researchers scouring the shadier corners of the internet (like the dark web) found 22 billion device and session cookie records – each of which could help to enable session hijacking. The situation is only getting worse. Once you understand how session hijacking truly works, it becomes clear why hackers choose this path to compromise data, commit fraud, and undermine trust.
What is Session Hijacking?
Session hijacking is a technique malicious actors use to gain unauthorized access to a legitimate user’s active session within an application. A session refers to the period of interaction between the user and the application, where the user’s identity and state are maintained across multiple requests.
In essence, session hijacking it’s about the attacker taking control of an authenticated session, which allows them to impersonate the victim, access whatever resources the victim can access, and carry out actions within the application without needing to authenticate themselves.
Modern web applications issue session tokens (stored in cookies or URLs) once a user logs in, in order to authenticate the user’s identity without requiring them to log in repeatedly. These tokens help maintain session continuity and are sent with every request. When attackers manage to capture or manipulate these tokens, they gain the same level of access as the authenticated user.
Here are some of the methods attackers use to hijack sessions:
1. Token Interception
Attackers can intercept session tokens if the network traffic is not encrypted (e.g., over HTTP instead of HTTPS). This method is typical in man-in-the-middle attacks, where attackers insert themselves between the client and your application server.
2. Session Sniffing
In session sniffing, attackers monitor unencrypted network traffic over unsecure connections like public Wi-Fi. Using packet sniffing tools, attackers can capture session cookies or tokens as they are transmitted in plaintext. Since the traffic isn’t encrypted (e.g., HTTP instead of HTTPS), the session data is exposed to anyone monitoring the network.
Session sniffing is a passive attack where attackers monitor unencrypted traffic to capture session data, while token interception typically involves actively intercepting or manipulating the session data during transmission.
3. Token Prediction
In a token prediction attack, attackers can hijack sessions by exploiting weak token generation methods, such as predictable sequences or timestamps, which allow them to guess or predict valid session tokens. If the system generates session tokens using a simple or repetitive pattern (such as sequential numbers or based on the time of day), attackers can predict the next valid token by analyzing the pattern.
4. Token Fixation
In a session fixation attack, an attacker manipulates or sets a session token for the victim to use. Once the victim logs in with the manipulated token, the attacker can use the same token to gain unauthorized access to the victim’s session, bypassing authentication measures.
5. Client-Side Attacks
Client-side attacks involve techniques that allow malicious code to run in a victim’s browser, enabling unauthorized access to session tokens stored in cookies or local storage. One standard method is exploiting web application vulnerabilities, such as Cross-site Scripting (XSS), to inject malicious code into a webpage, which the user unknowingly executes.
6. Man-in-the-Middle (MitM) and Related Techniques
Attackers also use a variety of advanced phishing techniques to hijack sessions, including Adversary-in-the-Middle (AitM), Browser-in-the-Middle (BitM), and Man-in-the-Browser (MitB). These techniques work by placing themselves between the user and the legitimate website, intercepting session data and bypassing multi-factor authentication (MFA) by relaying the authentication process in real time. By mimicking the legitimate site, they deceive users into entering their credentials, which are then used by the attacker to take over the session.
Adversary-in-the-Middle (AitM) attacks use a phishing proxy to intercept and relay communications between the user and the legitimate website, capturing credentials and session tokens. Browser-in-the-Middle (BitM) involves the attacker controlling the browser environment, allowing them to manipulate or intercept data directly. Man-in-the-Browser (MitB) uses malware to infect the user’s browser, modifying transactions and capturing session information without the user noticing.
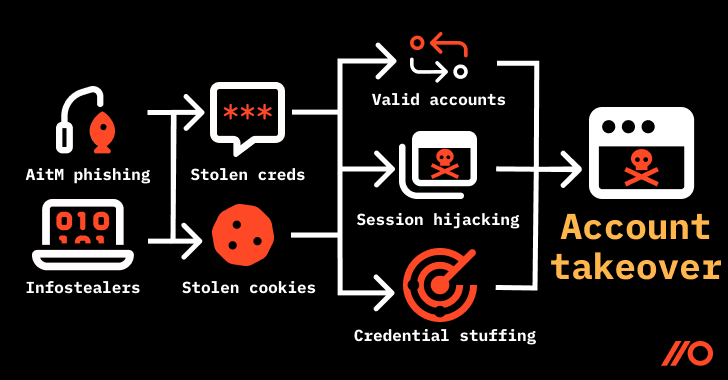
7. Infostealer Toolkits
Another modern trend—part of what some call session hijacking 2.0— involves infostealer malware, explicitly targeting browser data like stored session cookies, authentication tokens, and saved passwords. Infostealer malware typically finds its way to your browser through phishing emails, malicious downloads, or compromised websites. Once deployed, they can steal active session information from browsers, enabling attackers to log in without further authentication.
The Impact of Session Hijacking on Businesses
Like many types of cyberattacks, session hijacking can significantly affect businesses. Compromising user sessions exposes sensitive customer data, potentially leading to unauthorized transactions, identity theft, and account takeovers. These incidents erode customer trust and can result in immediate financial loss, increased operational costs for incident response, and long-term reputational damage.
Moreover, the unauthorized access gained through session hijacking often acts as a gateway for further attacks, such as malware injection or data exfiltration, putting additional sensitive information at risk. Businesses may face compliance issues if customer data is compromised, triggering fines under regulations like GDPR and PCI DSS. Ultimately, the fallout can strain budgets, affect customer loyalty, and damage partnerships.
8 Ways to Prevent Session Hijacking
1. Regenerate Session Tokens After Login or Privilege Changes
Regenerate session tokens after critical actions like user login or privilege escalation. By issuing a new, unpredictable token upon these events, you invalidate any existing tokens that may have been compromised and prevent unauthorized access. This practice ensures attackers can’t use an old session token to maintain access after a user’s security state changes.
Threat modeling can help identify vulnerabilities in the token generation process, allowing security teams to implement stronger mechanisms to reduce the risk of exploitation.
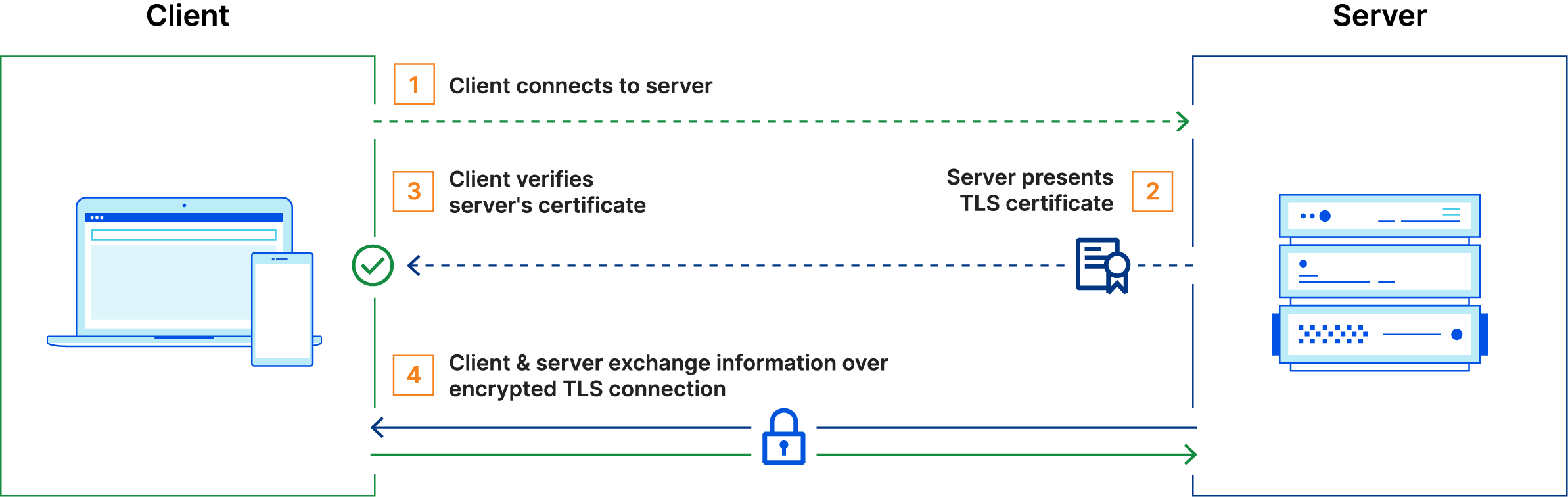
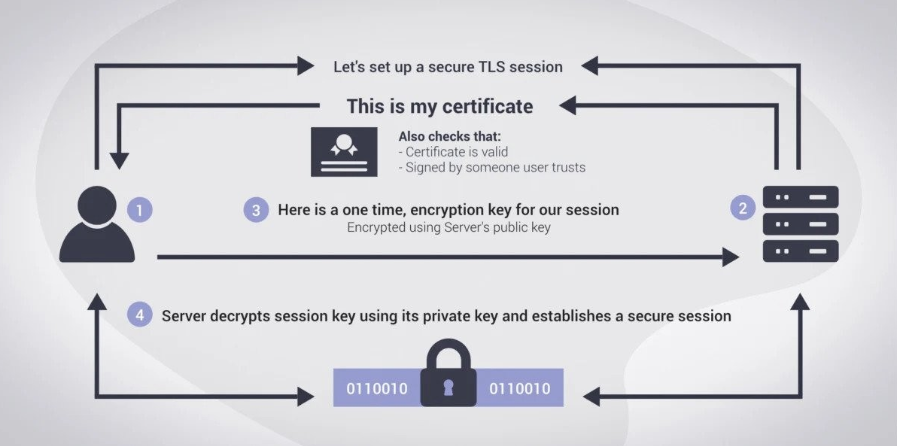
2. Adopt Mutual TLS for Client-Server Authentication
Implement mutual TLS (mTLS) to establish a secure channel where the client and server authenticate each other. Requiring client certificates ensures that only authorized devices can establish sessions.
This two-way authentication method reduces the risk of session hijacking through AitM attacks by fortifying the client-server trust relationship. While mTLS does not specifically target session hijacking, its implementation strengthens a system’s overall security architecture by making it more difficult for attackers to exploit vulnerabilities leading to session hijacking.
3. Log and Monitor Session Activities in Real Time
Continuously monitor session activities to detect anomalies that may indicate hijacking attempts. Unusual behaviors—such as simultaneous logins from different locations or a sudden change in user session patterns—can signal a compromised session. By leveraging machine learning algorithms or advanced analytics, you can flag these anomalies and respond quickly, cutting off attackers before they can cause damage.
4. Use Token Binding to Tie Session Tokens to Specific Devices
Implement token binding to enhance session security by cryptographically linking tokens to specific client devices. This technique involves binding session tokens to a private key stored on the client, requiring the client to prove possession of the key during each session request. By doing so, token binding prevents token misuse on unauthorized devices.
This technique adds a layer of security by requiring the client to prove possession of the private key associated with the token during session requests. Even if an attacker intercepts a session token, they can’t use it on a different device.
5. Limit Session Duration and Implement Idle Timeout
Restrict session duration to limit attackers’ window of opportunity. Set clear expiration policies to automatically log users out after a reasonable period of inactivity, reducing the chance of session hijacking from abandoned sessions. For a better user experience, consider providing timeout warnings, allowing users to extend their session if they are still active. This approach balances data security needs with a smooth user experience.
6. Encrypt Session Data
Encrypt session data in transit and at rest to protect it from interception. Use robust protocols like TLS 1.3 for encrypting session information during transmission, preventing attackers from eavesdropping or tampering with the data. Additionally, encrypt session storage in your backend systems to safeguard against breaches. This layered encryption approach helps secure the session token throughout its lifecycle.
7. Restrict IP Addresses for Sessions
Enforce IP address restrictions for active sessions to prevent unauthorized access from unexpected locations. By locking a session to a specific IP address or range, you can block attackers who attempt to reuse session tokens from different devices or networks. This method is particularly effective when users connect from known or controlled IP addresses, like corporate networks or trusted VPNs.
8. Implement Anti-CSRF Tokens
Cross-site request Forgery (CSRF) attacks can be an entry point for session hijacking. Anti-CSRF tokens help mitigate this risk by ensuring that every action a user initiates comes from a valid source. These tokens are unique to each session and validated with every request, making it difficult for attackers to execute unauthorized actions.
Stay One Step Ahead of Session Hijackers
Session hijacking is a go-to tactic for cybercriminals, offering a back door into user accounts and a shortcut past recommended security practices like MFA. As session hijacking attacks evolve, businesses face an increasing threat to their data, finances, and customer trust. The smarter hijackers get, the smarter your defenses must become.
Memcyco provides robust protection against impersonation attacks, which can serve as the entry point for session hijacking, by rendering fraudulent websites ineffective before attackers have a chance to steal sensitive data. But Memcyco doesn’t stop there. We’re actively expanding our capabilities to address all critical aspects of session hijacking and other evolving digital threats such as social media attacks, ensuring your business stays one step ahead of attackers. Learn more here.